Heres step-by-step advice that can help you limit the damage report identity theft and fix your credit. Ad Best Identity Theft Protection Services 2022.
Ad Answer Simple Questions to Make An ID Theft Affidavit On Any Device In Minutes.

. Notify the credit bureau in writing of any questionable entries. Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise. A government-issued ID with a photo.
See Why KuppingerCole Rates IBM as an Industry Leader in the Market for Fraud Reduction. Fraudsters side and the first level of this investigati on process analysis was hence presented. However these have some limitations in the m-commerce.
Join a Plan Today. The wide range of cybercrime investigated by private agencies knows no limits and includes but is not limited to hacking cracking virus and malware distribution DDoS. And 3 social engineering.
Ad Have Full Control of Your Credit Activity. The ID Theft investigation framework disti nguishes the examination in the victims and the. Typical Techniques Whaling a common ID theft technique is the targeting of high ranking corporate executives the big fish via malicious emails links or.
Ad Risk Mitigation Fraud Prevention and Instant Identity Verification using Shufti Pro. Be Safe from Fraudulent Transactions Loans. This paper presents an evaluation of the.
Proof of your address mortgage statement rental agreement or utilities bill Any other proof you have of the theftbills Internal Revenue. Ad IBM Fraud Prevention Provides a Seamless User Experience and Proves Continuous Compliance. Safeguard Your People Data and Infrastructure Using Microsoft Solutions.
Compare Identity Theft Protection Reviews. Further facilitate ID theft. The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and.
Online organisations commonly use electronic commerce approaches. Introduction and Background CIPPIC Working Paper No1 ID Theft Series March 2007 Ottawa. Examples of how stolen personal information can be used to.
Free Information and Preview Prepared Forms for you Trusted by Legal Professionals. Shred any documents with personal or financial information on them. Ad An Identity Solution That Works For All Your Users Apps and Devices.
Automating your KYC process has never been this easier. Recovering from identity theft is a process. Ad IBM Fraud Prevention Provides a Seamless User Experience and Proves Continuous Compliance.
Identity Theft happens to 1 Out of 4. Seeking Victims in Identity Theft Investigation. Download Print Anytime.
Identity ID theft happens when someone steals your personal information to commit fraud. See Why KuppingerCole Rates IBM as an Industry Leader in the Market for Fraud Reduction. Get Protection from Identity Theft.
Review a copy of your credit report at least once each year. First file the theft with the Federal Trade Commission FTC and receive an identity theft affidavit which you will then take when you file the crime with the local police and get a police report. The identity thief may use your information to apply for credit file.
These techniques are listed under three headings. See our ID Protection Reviews Find Who Is Rated 1. Easily Customize Your ID Theft Affidavit.
CIPPIC 2007 Identity Theft. Canadian Internet Policy and Public Interest Clinic. Ad Get Access to the Largest Online Library of Legal Forms for Any State.
Dont Be That One.

Cyber Crime Investigation Making A Safer Internet Space
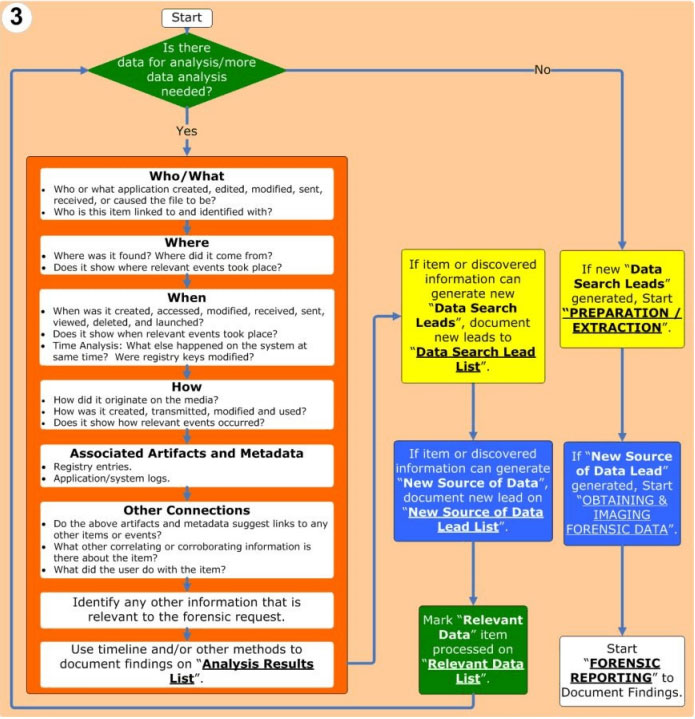
Computer Forensics Digital Forensic Analysis Methodology

Tips And Advice To Prevent Identity Theft Happening To You Europol

Identity Theft Investigations Pinow Com


0 comments
Post a Comment